Revolutionary Guards’ Cyber Attacks Now Directed at Rouhani Cabinet Members

IRGC Actively Recruiting Technical Experts to Staff New Hacking Team
April 26, 2016—Iran’s Revolutionary Guards, who have long waged cyber attacks against the country’s activists and journalists, have extended their hacking attacks to Rouhani administration officials, the International Campaign for Human Rights in Iran has learned, including close associates of President Hassan Rouhani and his cabinet members. To date, the Rouhani administration has not publicly criticized the Guards’ cyber attacks.
In the latest attack, Shahindokht Mowlaverdi, Rouhani’s Vice President for Women and Family Affairs, announced on Twitter and Telegram on April 20, 2016 that her Gmail and Facebook accounts had been hacked, and she asked her followers not to respond to any messages from the compromised accounts.
“The widespread breaches of private space through cyber attacks carried out by the Revolutionary Guards against journalists and civil activists for years has now spread to officials within Rouhani’s Administration,” said Hadi Ghaemi, the Campaign’s executive director.
“Given the broad extent of these attacks, the President and officials of the Ministry of Communications and Information Technology must take serious steps to put a stop to them and end violations of citizens’ rights in this field,” he added.
Over the past two years, several senior Rouhani administration officials have been the target of these attacks, including a close aide to Rouhani, a cabinet member, a deputy foreign minister, and former vice president Mohammad Ali Abtahi, causing them to temporarily or permanently lose control of their accounts.
The attacks are part of a sustained effort by a Revolutionary Guard-controlled cyber army, which is not under the control or authority of the Rouhani administration, to monitor and disrupt the online activities of administration officials and reformist figures, in addition to the civil activists and journalists who have long been the targets of such attacks. After the accounts are hacked, the contacts on those accounts also become targets.
Information gathered by the Campaign indicates that over the past year, one of the units of the Islamic Revolutionary Guards Corps (IRGC) has actively tried to recruit Iran’s cyber security experts, inviting them to cooperate in conducting cyber attacks and developing phishing tools, malware and Trojan files designed to infiltrate personal accounts.
“The IRGC unit offers high salaries to its recruiting targets and if they refuse to cooperate they are told that rejecting the offer will have ‘severe consequences,’” one technology expert, who was approached by the Guards, told the Campaign.
In every case, after an account has been compromised, hackers have tried to quickly target those on the compromised account’s contact list, especially opposition politicians and domestic and foreign journalists, in order to entrap them before the hacked account is exposed.
The Campaign’s investigation shows that Iran’s cyber army and other security agencies primarily employ three tactics in their attacks. Even though the tactics are not sophisticated, they are still effective because most users are uninformed about basic security precautions.
The most common tactic, known as “social engineering,” involves sending a fake login page to targeted individuals and tricking them into typing in their username and password. This phishing tactic allows attackers to easily take control of a person’s online account.
Those who hacked Vice President Mowlaverdi’s Facebook account had sent messages and emails to her contacts containing a link to a photograph. Clicking on the link opened a fake Gmail login page, and some of the contacts gave away their usernames and passwords and lost control of their accounts.
A number of those whose accounts were compromised told the Campaign that they had carelessly trusted fake log-in messages and requests for verification codes to be sent to their phones from the hacked accounts, thereby giving away their Telegram and Facebook accounts to hackers. (Image 3)
A second hacking tactic widely used during the recent parliamentary elections resulted in dozens of journalists and political activists losing their Gmail and Facebook accounts. Targets were sent a message to open a PowerPoint attachment containing “urgent news” about the disqualification of the grandson of the late Ayatollah Rouhollah Khomeini from the elections. (Image 2)
When targets opened the attachment it activated a malware that sent the computer’s information to the hackers. As long as the malware existed in the computer it would be under the control of the hackers, even if the victim changed passwords.
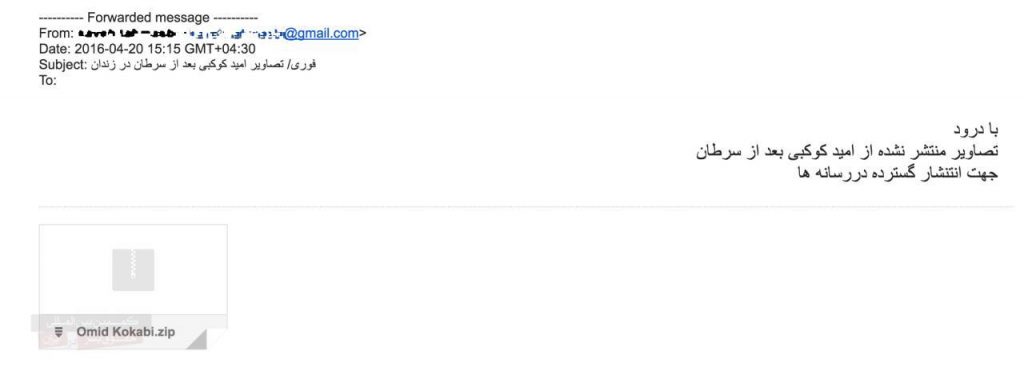
In a recent version of this tactic, the malware was embedded in a PowerPoint that was contained within a zip file. Emails were sent to activists and journalists with a zip file claiming to contain the most recent photographs of political prisoner Omid Kokabee, who has just had cancer surgery. Opening the PowerPoint within the zip file activated the malware. Frequently, hacking attacks will increase during news “events,” so that hackers can capitalize on interest in a particular event to spread the malware.
In some instances, when targets were not online, they received a phone call requesting them to open an important file in their email. Alternatively, they were told that their email account had been hacked and they should quickly change their password. In other cases, targets who had accounts with two-step verification, were asked to give the verification code sent to their phone.
A journalist who was targeted after an official’s account was hacked told the Campaign: “I received a message on Google Chat from one of my contacts who asked me to open a file. I became suspicious because I had not heard from that person in years. When I opened the message I saw that there was a link with a fake URL and I became convinced that the email was from a hacked account. Then I received a phone call from a number with a London prefix. The person calling complained that I had been sending him junk emails. I didn’t know the person and didn’t know what he was talking about. When I checked my Gmail, I saw an email from Google warning me about attempts to hack my account. But when I looked at the sender’s email, I noticed it said ‘qooqle.com’ instead of ‘google.com.’ It was another hack attack on my account.”
The third tactic, more frequently experienced by Iranians in recent weeks, involves intercepting phone messages to steal verification codes sent to users who want to change the password on their Facebook, Gmail or Telegram accounts.
Image 1: The hackers who control Mowlaverdi’s account post messages asking users to open a link that launches a phishing attack.
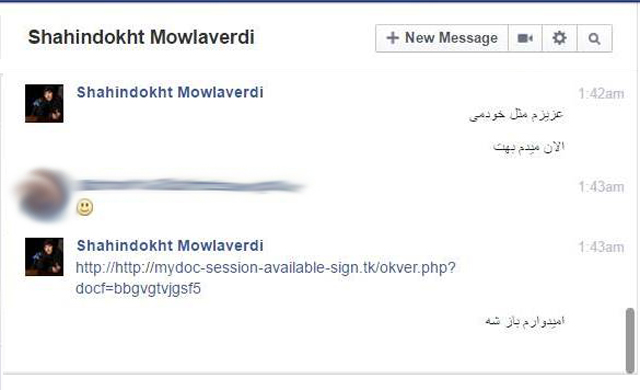
Image 2: Malware attack during elections for the 10th parliamentary session.
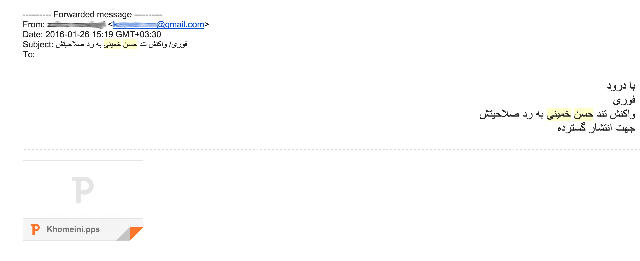
Image 3:
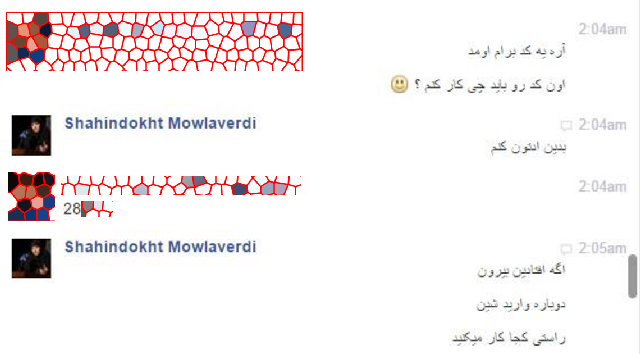
Image 4: