Negligence by Major Tech Companies like Google and Telegram Aiding Iran’s Cyber Army
Tech Giants’ Failure to Implement Security Measures Endangers Millions of Users
Large technology firms are failing to provide sophisticated and country-specific user security measures, and as a result, are helping Iran’s state agencies target Iranian citizens online, an investigation by the International Campaign for Human Rights in Iran has found.
By not upgrading their security protocols and denying Iranian users access to the latest technology tools and services to protect themselves, tech giants including Google and Facebook are inadvertently allowing Iranians to fall victim to attacks by government hackers.
Tech companies—including Telegram, Iran’s most widely used social messaging app—have demonstrated a lack of understanding of Iran’s state-controlled Internet as well as the government’s systematic efforts to violate the privacy of online users.
Online security is of critical importance in Iran; many individuals have been arrested, prosecuted and convicted for their peaceful online activities and are serving lengthy prison sentences under catchall national security charges for online content with which the authorities disapprove.
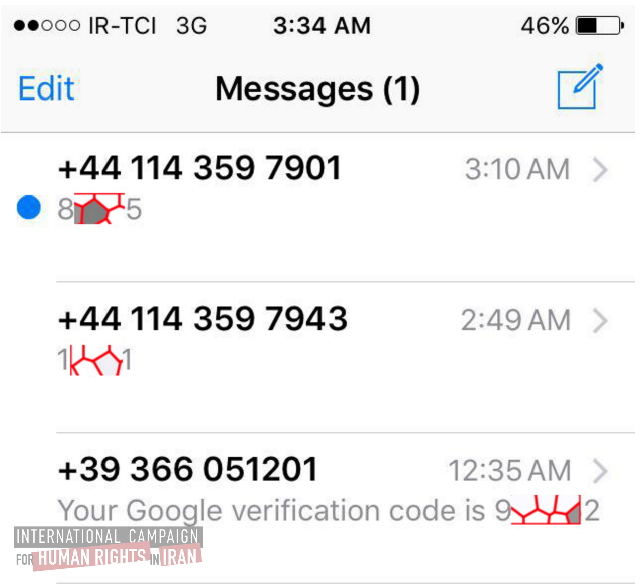
This screens shot shows an example of received messages from Telegram and Google that users did not request, but rather were requested by hackers.
State agencies can access all of Iran’s communications networks, so if the email service Gmail sends a text message with a pass code to a user’s phone that would enable the user to access their Gmail account, the text message could be intercepted and read by state hackers who could then break into the account.
While publicly arguing that they take user security very seriously, tech companies have so far failed to show any serious interest in minimizing security threats to Iranians.
Increasing Attacks
Threats against the privacy and security of online users in Iran are serious and growing. Cyber attacks on the Gmail, Telegram and Facebook accounts of Iranian journalists and political activists increased dramatically following Iran’s February 2016 elections, which saw widespread online campaigning. These violations of user privacy have included attacks where state-employed hackers have requested text messages from email and social media apps and intercepted the texts, which enable access to the accounts, by monitoring users’ cell phones.
“One night, around 2 in the morning, I got a phone call,” a journalist told the Campaign. “It was late and I didn’t pay attention to it. Minutes later I received a short text from Telegram with a five-digit code. I hadn’t requested the code so I became suspicious. I immediately called an expert and he told me state hackers have been trying to get into my Telegram account.”
State demands for the owners of social messaging apps to save Iranian users’ data on servers inside Iran is yet another indication of growing efforts by the government to monitor and control domestic traffic. By neglecting to adequately protect Iranian user data, tech giants are undermining personal security and effectively encouraging state hacking.
The Campaign has called on all major tech companies to take advantage of the U.S. government’s General License-D and grant Iranian users access to the latest personal communications tools and services that strengthen online and digital account security. Taking this step could help prevent cyber attacks on Iranians that result in users being imprisoned.
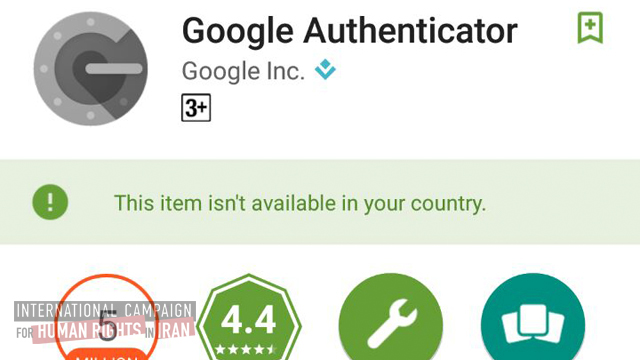
This screen shot shows that Google Authenticator is blocked to Iranian users due to sanctions against the Islamic Republic.
Investigations by the Campaign show that between March and April 2016, dozens of journalists, political activists and artists were targeted by Iran’s cyber army while the users’ activities on Telegram were closely monitored.
On April 28, 2016, Telegram CEO Pavel Durov tweeted that users in countries like Iran should enable 2-step verification, which requires two verification conditions to be satisfied for a login attempt to be successful. But Iranians whose accounts have been hacked told the Campaign that they had already enabled 2-step verification—indicating state hackers have found a way to get around this security measure.
Even Telegram’s encrypted “secret chat” service, which two users can utilize to communicate, becomes vulnerable when one user loses control of his or her account.
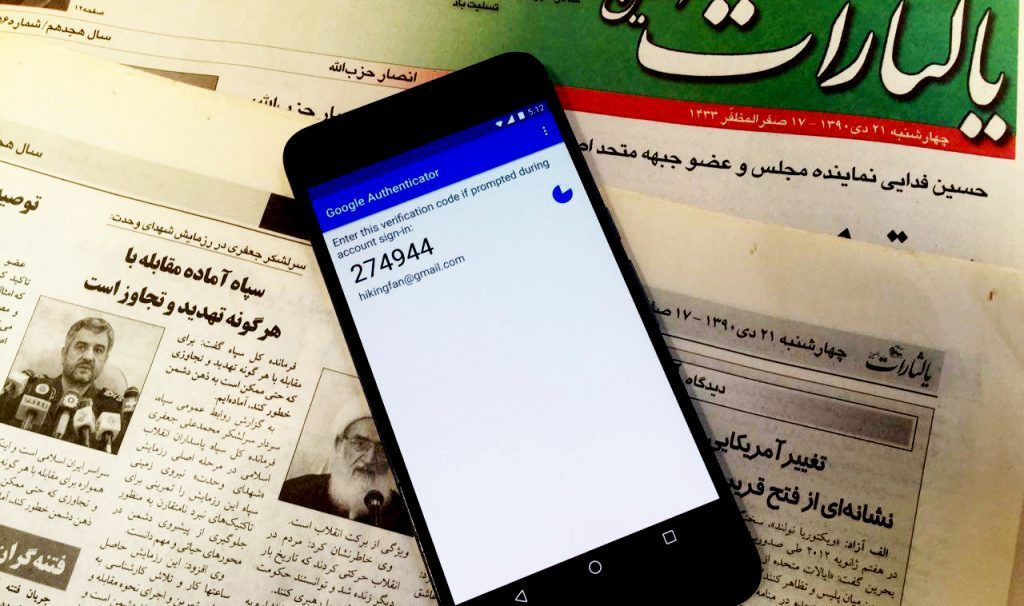
The most common hacking method in Iran works through the interception of text messages containing codes that would enable users’ access to their accounts. Google has a more secure verification app, known as the Authenticator, which does not require sending pass codes via text. The app, which can also be used for more secure account verification on other sites such as Facebook, is not available to users in Iran due to U.S. sanctions.
“I tried to use Google’s Authenticator, but unfortunately because of the sanctions on Iran I have not been able to download it,” a journalist who became a victim of a cyber attack told the Campaign. “These sanctions are endangering our personal security.”
![This is how state hackers access an account after intercepting a text message containing a pass code.]](https://iranhumanrights.org/wp-content/uploads/ActiveSession.jpg)
This is how state hackers access an account after intercepting a text message containing a pass code.]
Google’s refusal to grant Iranians access to more sophisticated verification services only enables Iran’s cyber army to continue and expand their attacks on the personal security of Iranian users.






